Cyber Security Solutions
We offer Cyber Security Assessments that identify potential risks, identify vulnerabilities, and address process improvements to strengthen your security in line with industry standards.
The goal of protecting your business’s data and securing the infrastructure is to establish effective security practices that address critical business requirements. Performing a cyber security assessment is the best way to identify weak points, manage security risks, and help meet compliance requirements.
65,000+ cyber attacks are committed annually against businesses. Keeping your business secure through cyber security assessments is essential for ensuring basic cyber hygiene, and it provides protection against the catastrophic implications of cyber-attacks. Data breaches can cost SMEs £50-£150k and larger organisations can cost upwards of £500k.
Our tailor-made Cyber Security Assessment is designed to reduce security risks and improve compliance. Our cyber security experts are fully qualified and understand internal and external threats that face businesses.
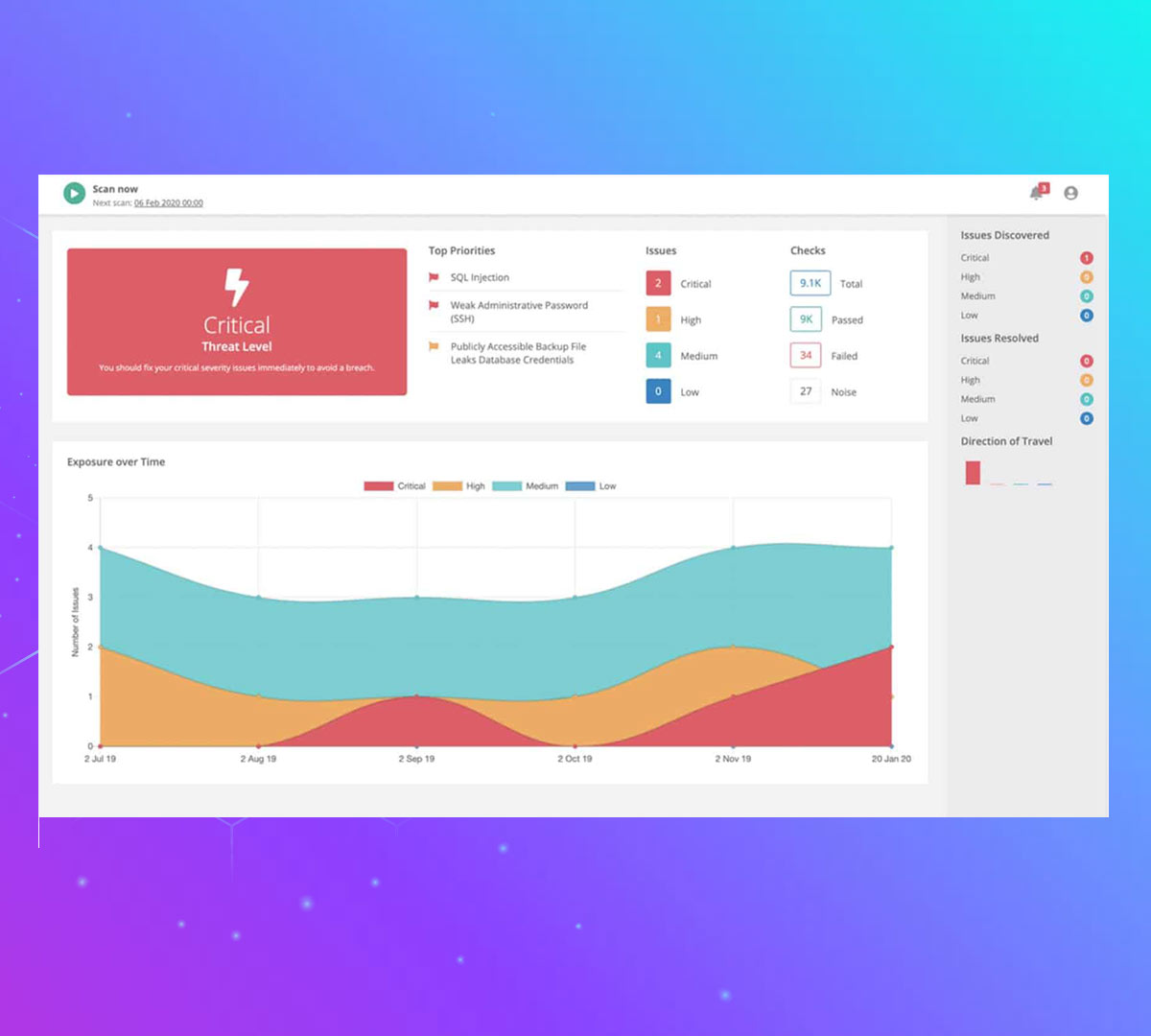
The essentials for bullet-proofing your Cyber Security
Public Discovery Testing (Free)
We offer this as a free of charge service to help businesses understand the level of risks they might be exposed to as a result of having improper control over the information published on the internet.
Public Discovery Testing is performed to collect personal and/or sensitive data about the company that is publicly available.
This information is usually accessible to every internet user. Such information is then tested with the possibility of data theft in mind. In a simple and quick way, this activity exposes basic security risks that the organization may be open to from the outside world.
Vulnerability Assessment (Recommended)
Discover, identify and classify the vulnerabilities and security weaknesses in the organisation’s computer, network, or communications infrastructure.
Vulnerability Assessment provides an insight into an organisation’s current state of security, and the effectiveness of its countermeasures.
This would be a must and is included on all our assessments.
Basic Penetration Testing (Optional)
A penetration test is a simulated cyber attack against your computer system to test the security controls of your organisation and to check for exploitable vulnerabilities.
The Penetration Test simulates the attacks which a hacker might undertake to exploit the weaknesses in your organisation’s network and applications.
This service identifies external and internal vulnerabilities which would give access to the critical assets of the organisation. The Penetration Test validates the configurations of IT Assets and produces a list of known vulnerabilities present in the systems and applications. These findings are used to mitigate weaknesses before they are exploited.
Web Application Scanning
Also referred to as web application vulnerability scanning, is an automatic security program that searches for software vulnerabilities within web applications.
The software first crawls and builds a software construct of the entire website. This gives the scanner an insight into the application, which then performs automatic audit for common security vulnerabilities by launching a series of web attacks. The consultants then manually verify these security vulnerabilities.
It would be positioned to check for vulnerability code that has been introduced to the SharePoint Extranets.
Benefits of our Cyber Security Services
Enjoy peace of mind with 24/7 proactive protection
The right solution for your threat profile
Cyber protection built for you
Cost reduction
Are you using Microsoft 365 to its full potential?
Microsoft 365 Certified Experts

Transition to the Modern Workplace.
We’re here to help.
While a majority of businesses are effectively using Microsoft tools and Office 365, only a few of them have realised its full benefits. If you intend to take advantage of everything Microsoft 365 has to offer, then you can reach out to our certified experts. We offer a free assessment to identify gaps and improvements within your IT setup.
